Trends Directory
Find trends of anything. For Affiliates by Affiliates.
ANY.RUN’s Malware Trends = your light-speed malware awareness engine
It provides curated, technical, and dynamic malware insights—complete with behavioral analysis and IOCs—to help you detect, defend, teach, and hunt with up-to-date intelligence.
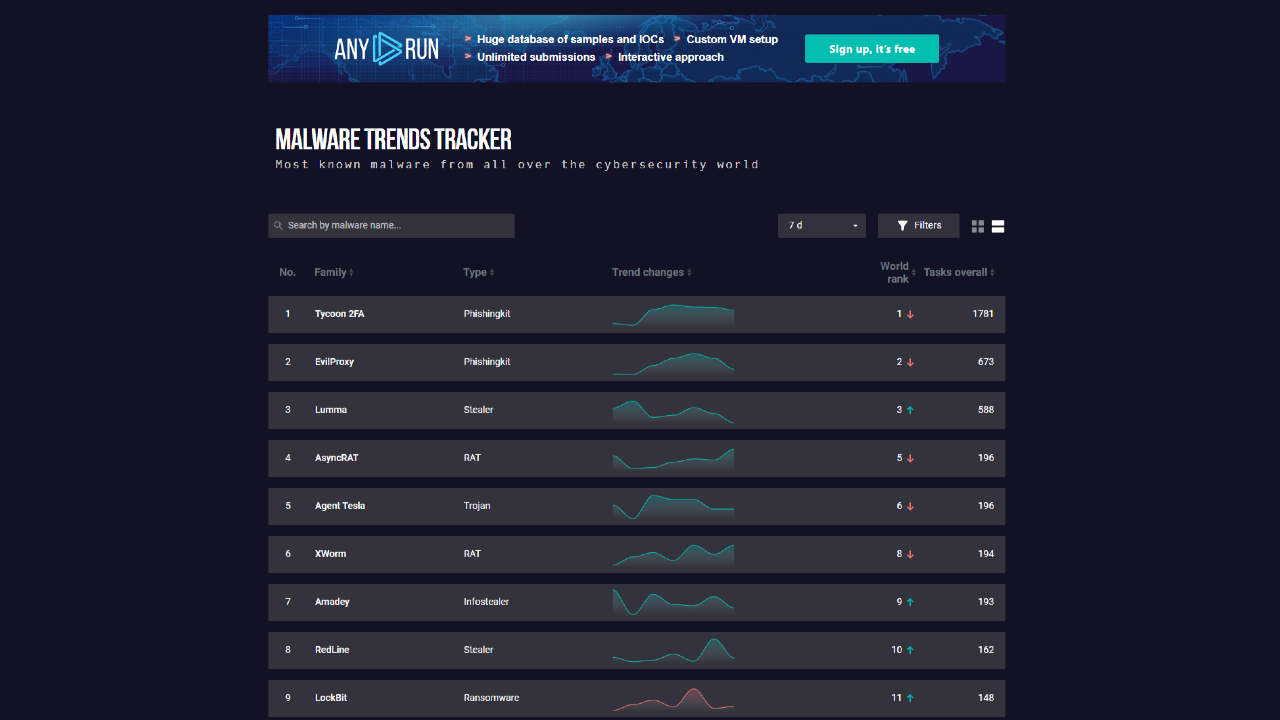
🛡️ Why ANY.RUN’s Malware Trends Should Be in Your Toolkit
ANY.RUN’s Malware Trends delivers constantly updated, dynamic articles tracking the latest malware campaigns, attack techniques, and payload variants. It empowers analysts, security engineers, and threat hunters with fresh intelligence—making malware threat awareness faster, clearer, and easier to act upon.
🧠 Standout Features
| Feature | Description | Benefit |
|---|---|---|
| Dynamic Trend Articles | Regularly updated content on emerging threats and malware strains | Stay current without scouring multiple threat feeds |
| Malware Family Coverage | In-depth analysis of ransomware, trojans, spyware, botnets, etc. | Get specialized info on high-risk or niche strains |
| Technical Breakdown | Includes IOCs, attack vectors, payload behavior, mitigation steps | Enables rapid threat response, threat hunting, and education |
| Interactive Sandbox Demos | Some articles include sandbox runs with interactive playback | See real-time execution to strengthen analysis and detection |
| Searchable Archive | Browse by family, date, severity, or sector | Easily access historical context and trends |
🛠 How to Use Malware Trends Effectively
| Step | What to Do | Why It Helps |
|---|---|---|
| 1. Check “Latest Trends” | View the newest articles on emerging threats | Fast-tracks awareness of immediate security concerns |
| 2. Filter by Malware Type | Use filters for ransomware, Android malware, ICS, etc. | Focus on threats most relevant to your environment |
| 3. Read the Technical Breakdown | Study IOCs, samples, infection chains, and detection rules | Enables immediate defense or threat-hunting actions |
| 4. Use Interactive Demos | Step through sandbox runs (if available) | Visualize real payload behavior for detection tuning |
| 5. Archive Research for Context | Compare current threats to historical strains | Spot evolution, attribution, or repeated patterns |
📊 Key Metrics & Indicators
| Metric / Indicator | Description | Use Case |
|---|---|---|
| Malware Family | Ransomware, trojan, worm, trojan, etc. | Prioritize defenses for high-risk families |
| First Seen / Update Time | When the article was published or refreshed | Target response to truly fresh threats |
| Severity Classification | Based on impact, scope, or sophistication | Prioritize handling of high-severity threats |
| IoC Presence | Presence of file hashes, IPs, domains for detection | Feed your SIEM or detection logic with curated intelligence |
| Payload Behavior Notes | Snapshot of network, file, process behavior | Aid detection profiling and response annotation |
📋 Real-World Use Cases
| Use Case | Description | Ideal For |
|---|---|---|
| Threat Hunting | Use real IOCs and sandbox observations to search your logs | SecOps teams, IR professionals |
| Incident Response | Quickly triage incidents using fresh behavioral patterns | CSIRT/SOC teams |
| Vulnerability Assessment | Link malware to exploited CVEs and assess patch needs | AppSec and IT Risk teams |
| Security Education | Teach with real examples, screenshots, IOCs, and sandbox videos | SecOps trainers, educators |
| Detection Development | Build YARA/Sigma rules or Snort signatures | Threat intel engineers, detection teams |
👥 Who Should Use Malware Trends?
| Role | How They Benefit |
|---|---|
| Threat Analysts & Hunters | Identify immediate threats and IOCs |
| Incident Responders | Gain fast, accurate context for emerging malware |
| Security Engineers | Build detection capability based on real payload behavior |
| SecOps Teams & Analysts | Stay alert to shifts in malware techniques |
| Security Educators | Teach real cases and hands-on malware behavior analysis |
✅ TL;DR
ANY.RUN’s Malware Trends = your light-speed malware awareness engine. It provides curated, technical, and dynamic malware insights—complete with behavioral analysis and IOCs—to help you detect, defend, teach, and hunt with up-to-date intelligence.
Need help building a detection rule dashboard, threat-hunting playbook, or training modules using these trends? I can draft a custom framework next!
